Hiding your identity on the Internet using a Linux-based operating system is really very simple, and all this without having to hire a VPN service like those that exist today. Distributions like Kali Linux are used to audit the security of WiFi networks, web, servers etc. However, operating systems such as Debian or Ubuntu are also widely used for these tasks. Today in RedesZone we are going to teach you step by step how to hide your identity when browsing the Internet, making use of Tor and also the Proxychains tool for Linux.
What is Proxychains?
Proxychains is a tool that acts as a proxy server supporting protocols such as HTTP, HTTPS, SOCKS4 and SOCKS5, which works on Linux-based operating systems, on BSD and also on macOS. This tool allows any TCP connection made by a local program to go to the Internet through a series of configured proxies to its destination. In this way, our traffic could go through one or more proxies to anonymize our identity on the Internet, hiding the public IP address that our operator provides us, and going to the Internet with the public IP of the last proxy to which we have connected.
Some very interesting features of this program are that it will allow us to chain several types of proxies simultaneously, be they HTTP or HTTPS, SOCKS4 and SOCKS5 proxies. In addition, we will be able to configure different traffic tunneling options, allowing to define several proxy servers and for the program itself to choose them randomly, strictly in the configuration that we have defined, dynamically and also in "Round Robin" mode. Proxychains is capable of resolving DNS requests (which works with UDP) through the proxy, so DNS resolutions will also be anonymous.
Finally, proxychains allows you to define a maximum number of chained proxies. We must take this last aspect into account, the more proxies we chain, the greater our anonymity will be because the traffic is "jumping" from one server to another, however, the performance we will achieve will be really low, both in terms of speed and latency ( connection latency will be very high).
Thanks to the use of the Tor network, we will be able to configure the Tor network in Proxychains to go to the Internet through this anonymous network, without the need to use specific software such as Tor Browser that serves to browse the Tor network without having to configure anything more on our team.
Installing Tor and Proxychains on Linux
The first thing we must do is update the system with the patches and with the latest applications, for this we will open a terminal and type:
sudo apt update && sudo apt upgradeWe will wait for the repositories to update and all updates to install before continuing with this process. Once our system is updated, we will install Tor in it from the same repositories by typing:
sudo apt install tor proxychains
Once we have installed the two packages necessary to make anonymous connections, we must enable the Tor module, indicating the following command:
sudo service tor startAnd we check that it has started correctly with:
sudo service tor status
Now that we have the Tor service activated, we are going to make the necessary configuration in Proxychains to go to the Internet using the Tor network
Proxychains configuration to exit by Tor
With Tor already started we are going to modify the Proxychains configuration file, for this we will type:
sudo nano /etc/proxychains.confOnce we have opened the configuration file, we will be able to see all the configuration already made, and we will have to configure different advanced parameters to adapt it to our use.
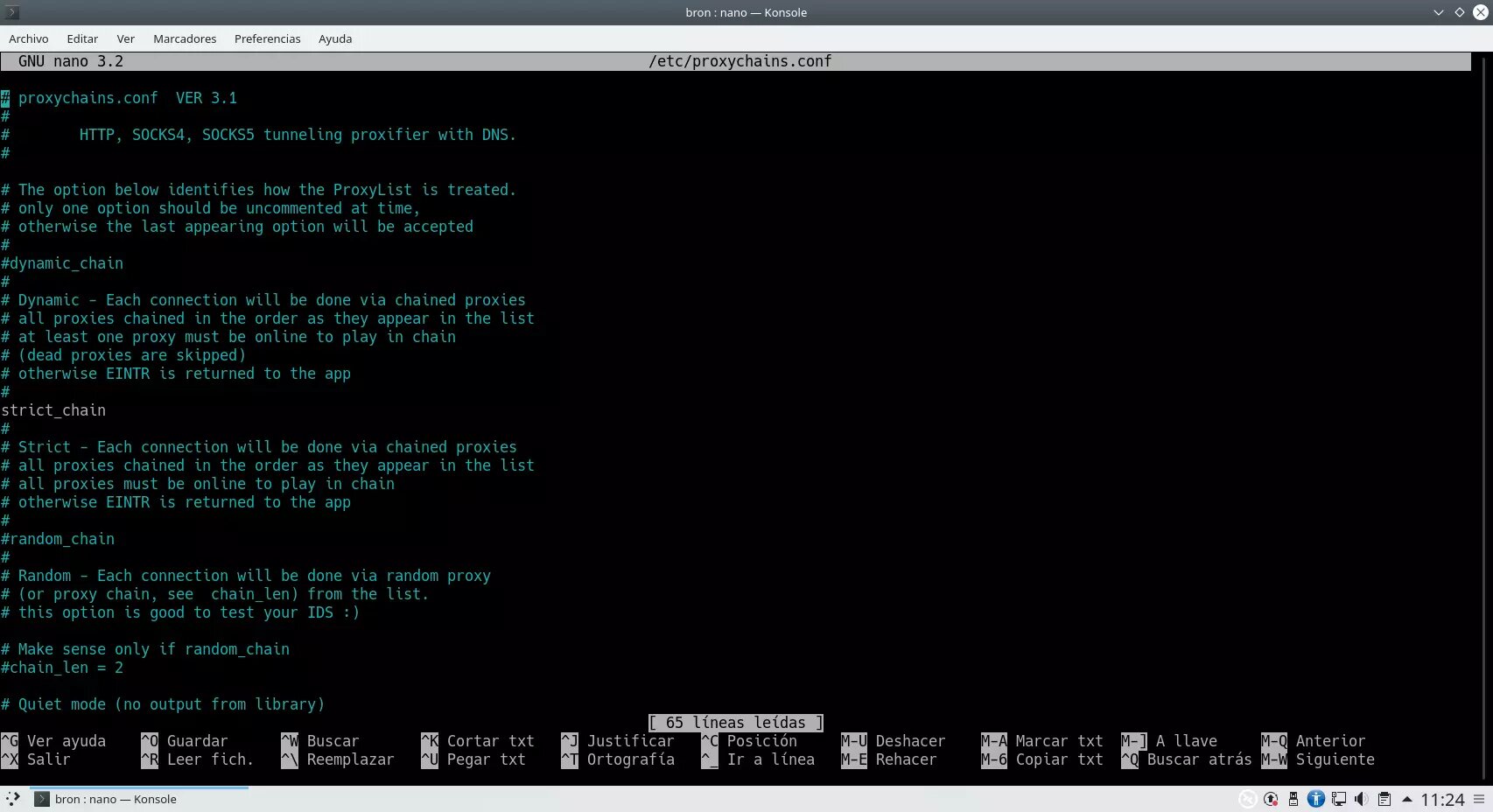
In this file we must make the following changes:
-
Uncomment by deleting the # dynamic_chain line, in this way, the chain will be dynamic.
-
Comment with a # the strict_chain line, in this way, the chain will not be strict.
The configuration would be as follows:
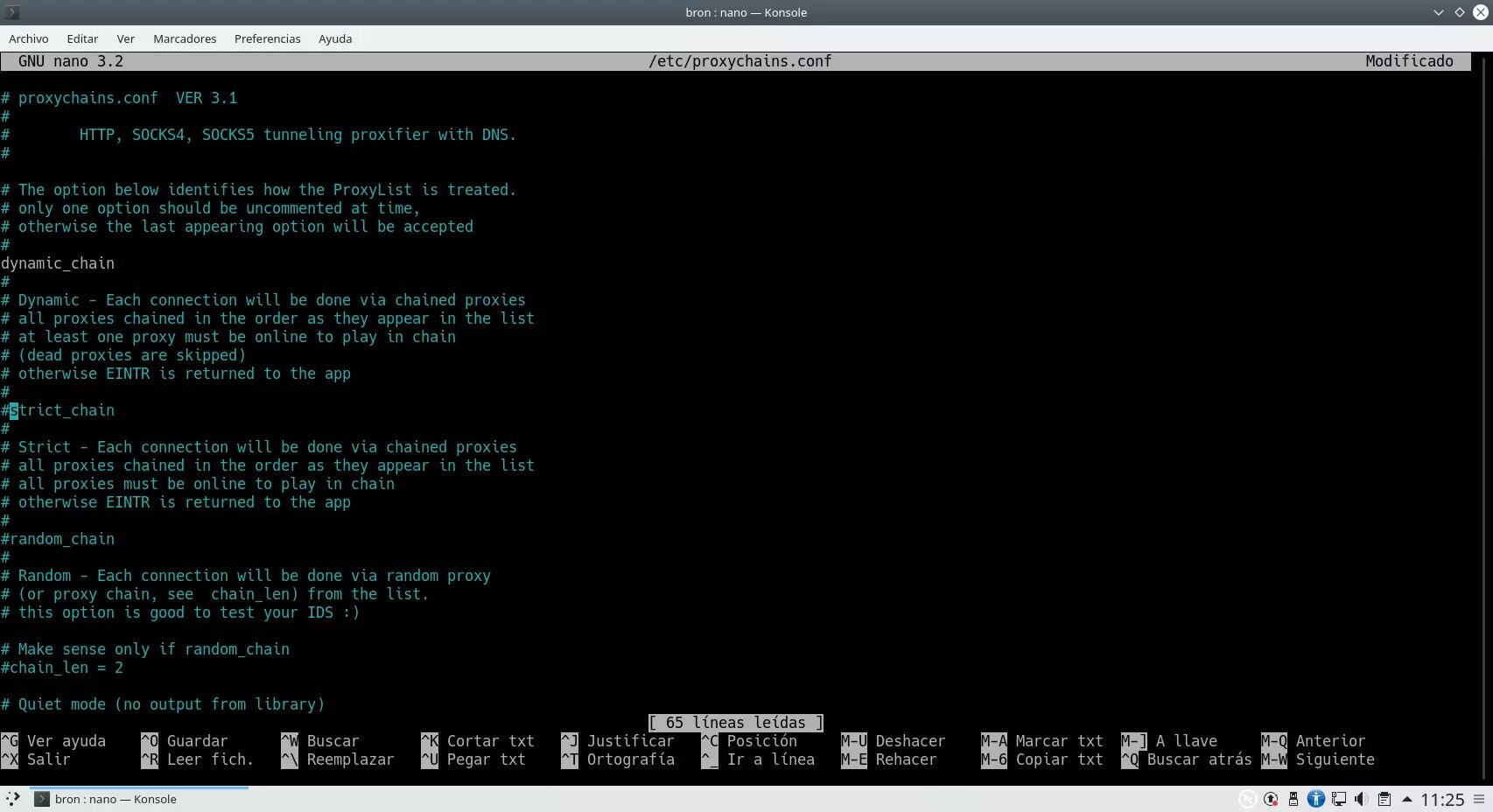
As you can see, we can configure the following parameters:
-
Dynamic_chain: the chain of proxies will be dynamic.
-
Strict_chain: the chain of proxies will be static as we have defined.
-
Random_chain: the chain of proxies will be random.
-
Chain_len: chain length, maximum 2 or whatever you want.
Now we will have to make a very important additional configuration, and that is to configure the SOCKS5 that we want, to do this, we will have to place this configuration at the bottom: "socks5 127.0.0.1 9050"
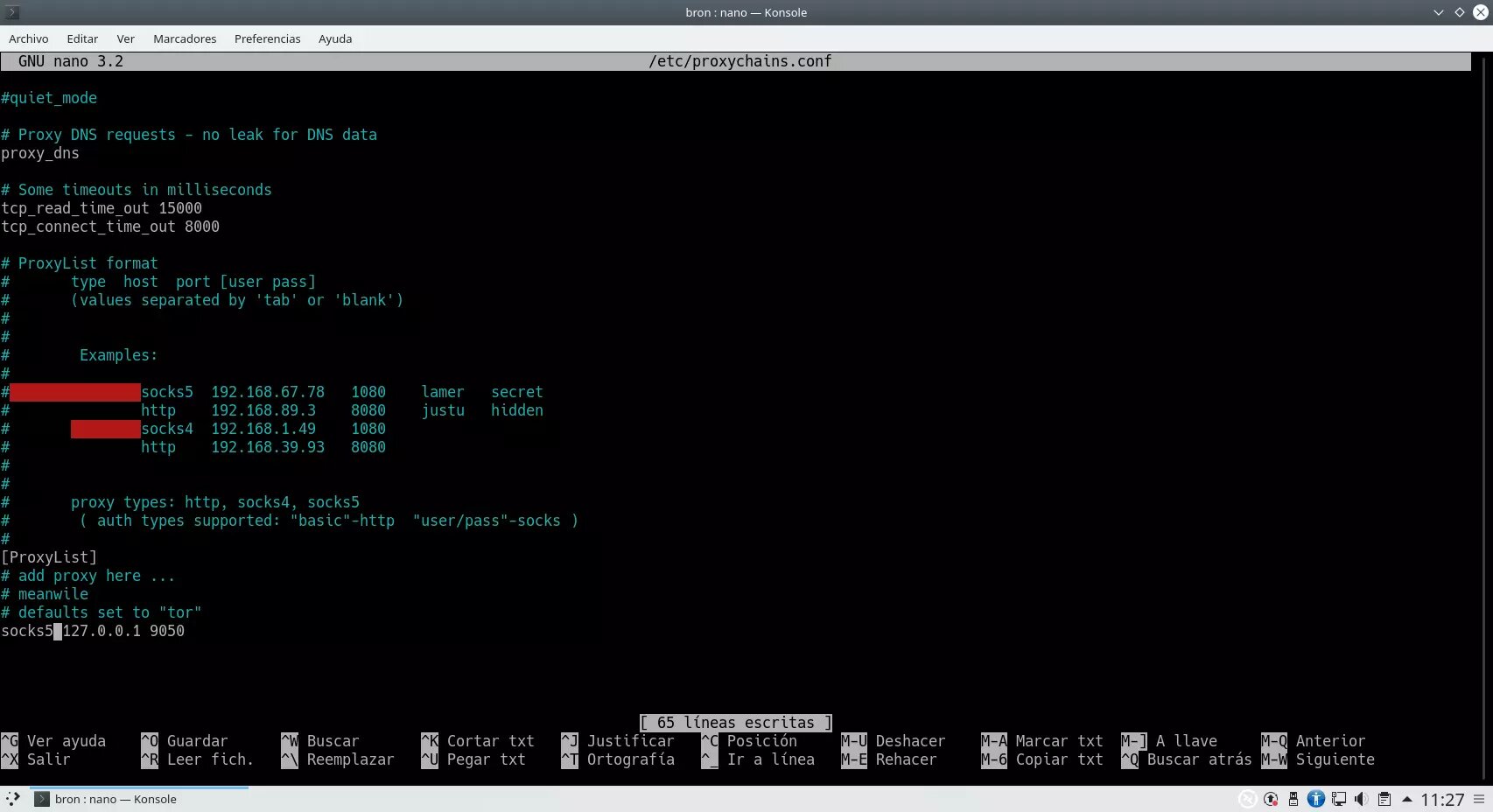
Other configurations that we can make in this section would be:
-
Proxy_dns: if we want the traffic of the DNS requests to also go through the proxy, to avoid data leakage.
-
tcp_read_time_out and tcp_connect_time_out are internal parameters, it is recommended not to touch it unless you know what you are doing.
Of course, we can configure the list of proxies just below, either HTTP, sock4 or socks5, in addition, in the event that the proxy needs some type of authentication, we will also be able to indicate it to connect directly.
With these steps we have everything ready to launch the web browser using proxychains to go to the Internet through the tor network.
Run web browser or programs with proxychains
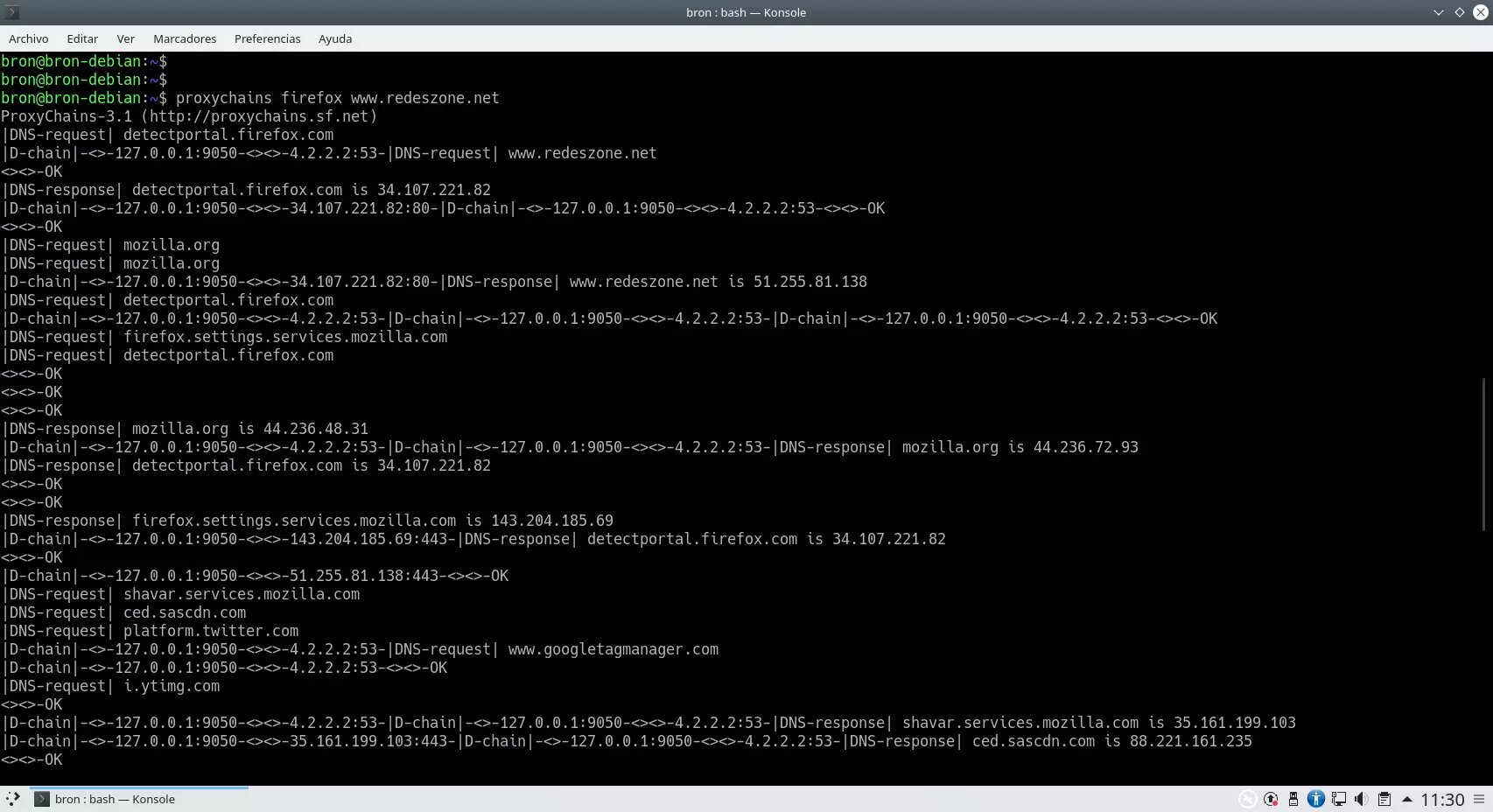
Once we have proxychains configured, now we will have to run the web browser using proxychains, for example, we could execute the following command to open a specific website through the Tor network:
proxychains firefox www.redeszone.netWhen executed, in the console we can see everything that proxychains is doing internally:
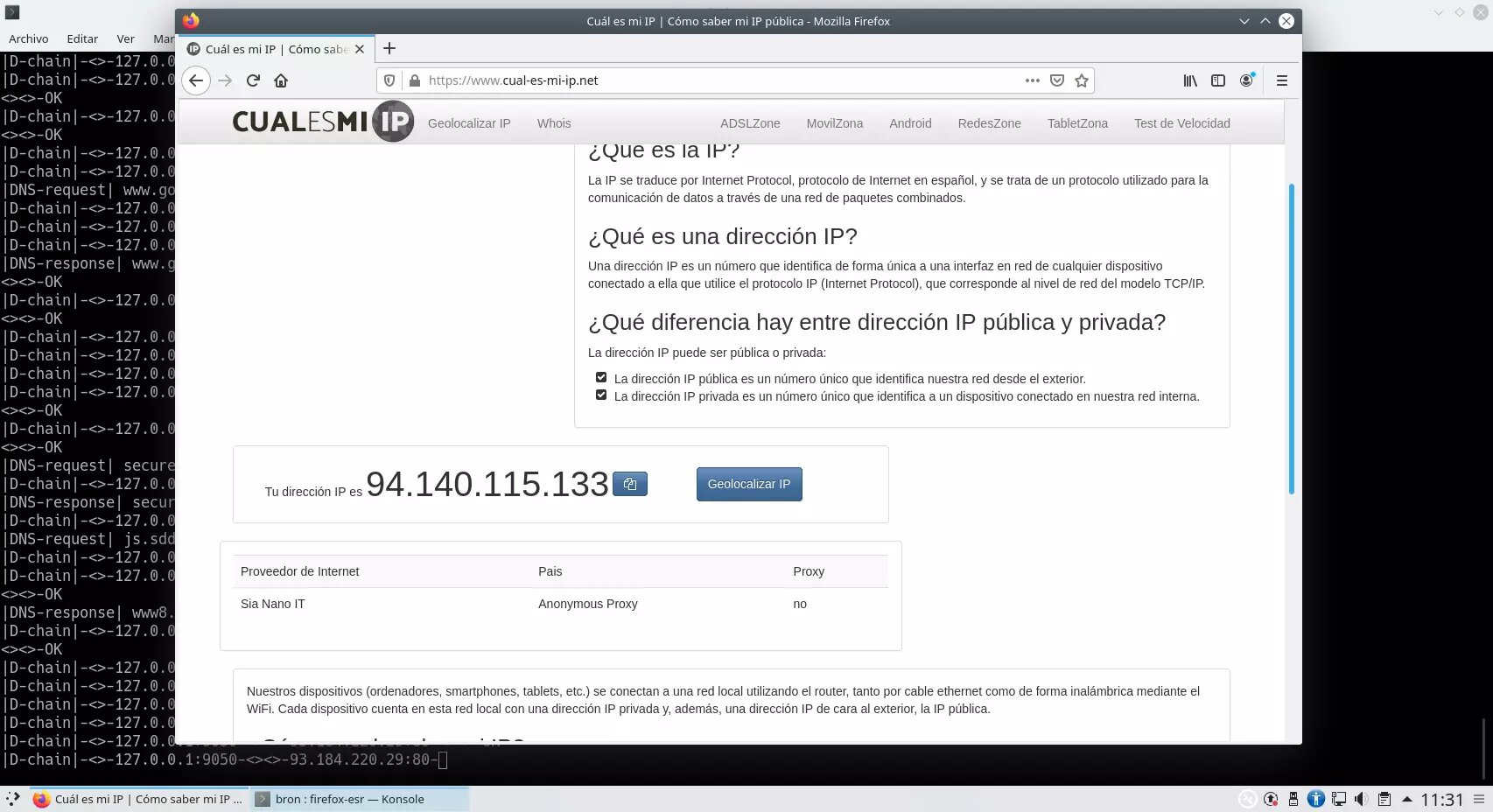
And check from which-es-my-ip.net that the IP we obtain is not the same as the one we actually have in our connection, but is obfuscated by the Tor network.
From now on, all the traffic that we generate in the browser window opened from the previous command will be totally anonymous, being able to establish a direct non-anonymous connection from any other window that we open manually from the same browser.
In the event that you want to run any other program with Internet access through this proxy that we have configured, you will simply have to run "proxychains" followed by the program that we want. For example, proxychains is widely used by pentesters to perform port scanning remotely anonymously, in this way, if we execute:
proxychains nmap -p 53 8.8.8.8We can perform a port scan based on the proxy that we have configured, in this way, our real public IP address will not appear, but the one of the configured proxy.
We hope that with this tutorial you can browse and perform different actions on the Internet anonymously, using the Tor network or any other anonymous proxy server that we can configure in this powerful and easy-to-use Proxychains program.





