Improve your network cleanliness with Bogon filtering:
By filtering Bogon IPs using our free Bogon referral community service, you will significantly reduce the risk of DDoS attacks and malicious traffic, ensuring a more robust and reliable network.
Ensure network integrity:
Bogon IPs are not valid for public internet traffic. By filtering them, you ensure that only legitimate traffic flows through your
network, improving its overall integrity.
Stay up to date to achieve maximum efficiency:
The Bogon and Full Bogon IP landscape is constantly evolving. Use our real-time BGP sessions to keep your lists up to date and optimize your network's defense mechanisms.
Strengthening measures against identity theft:
The addition of bogon filtering amplifies your network's anti-spoofing capabilities, making it more resilient to deceptive traffic sources.
Safety measures planned:
FILTERS FOR INCOMING AND OUTGOING PREFIXES FROM EACH ASSOCIATE. Every time you change, add or remove a prefix or IPv4 block, you must report it for an update.
We Avoid Undesirable trombone prefixes may be common due to poor practices in route advertising with filters at our exchange points as well as security mechanisms that may be complementary to customer security systems.
Requirements:
It is only necessary to have a public IP in version 4 and/or version 6 on the interconnection equipment with your provider to establish the announcement of routes via eBGP.
Inform via WhatsApp or email to This email address is being protected from spambots. You need JavaScript enabled to view it. the details of your organization (company) with these data:
-
COMPANY NAME:
-
RUC / IDENTIFICATION NUMBER:
-
CONTACT NAMES:
-
EMAIL:
-
CELL PHONE NUMBER:
-
COUNTRY / PROVINCE / DISTRICT / CITY:
-
SERVICE OPERATOR NAME:
-
IP OF THE EQUIPMENT TO USE BGP (IPV4 / IPV6):
-
IPS BLOCK ON THE EQUIPMENT TO USE BGP (IPV4 / IPV6):
You will find the settings to use below. Don't forget that your password will be updated.
Information and settings: Send Whatsapp https://ixp.org.pe/whatsapeame
Mitigate DDoS attacks at the source, as a team.
Get back to business as usual with the world's largest DoS mitigation community.
A BGP-based service that is an effective tool to help mitigate large, concentrated DDoS attacks.No ASN required, adds support for FlowSpec, IPv6, increased IPv4 and IPv6 advertisement sizes, improved reliability with redundant peering sessions, and ROAs are respected.
Mitigating DDoS attacks as a community
UTRS v2.0 uses techniques like remotely activated black holes (RTBH), but globally. Together, we enable you to protect yourself while helping protect the Internet. You help your neighbor, and they help you.
Become an Internet Hero
Join our community of over 1,300 network operators worldwide to fight against DDoS attacks. Be a hero and help protect the Internet.
DDoS mitigation services for network operators and Internet Service Providers (ISPs)
Unwanted Traffic Removal Service (UTRS)
-
Protect your network from disruptive criminals without the financial burden
-
Working as part of the global community to mitigate DDoS attacks
You will find the settings to use below. Don't forget that your password will be updated.
Information and settings: Enviar Whatsapp https://ixp.org.pe/whatsapeame
Welcome:
-
LIMA, PERU
-
CERRO DE PASCO, PERU
-
CAJAMARCA, PERU
-
OXAPAMPA, PERU
-
PASCO, PERU
-
JULIACA, PERU
-
QUITO, ECUADOR
-
SANTO DOMINGO, REPUBLICA DOMINCANA
-
SULLANA, PERU
-
NUEVA CAJAMARCA, PERU
-
JAEN, PERU
-
YURIMAGUAS, PERU
-
TRUJILLO, PERU
-
HUANTA, PERU
What is BGP? | BGP Routing Explained
Link: https://nocperu.com/es/component/content/article/8-noticias/1047-que-es-bgp-enrutamiento-bgp-explicado?Itemid=158
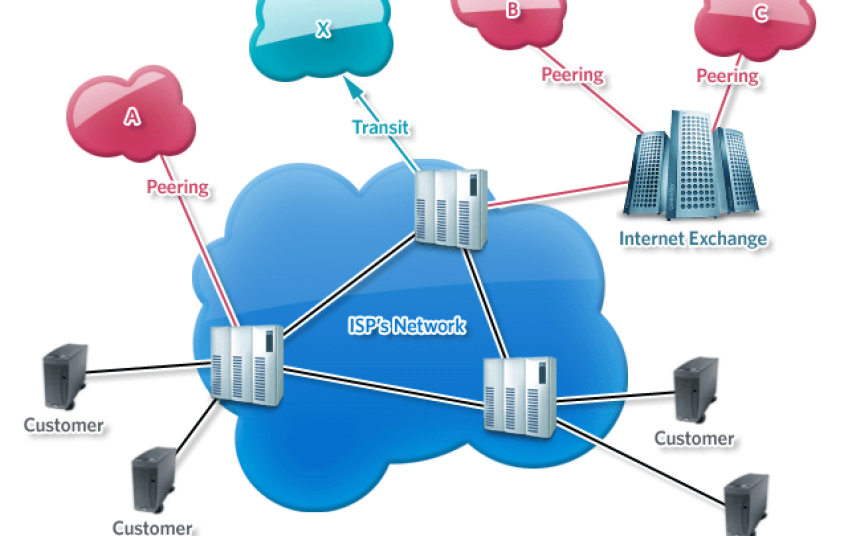
Explanation: What Is Internet Peering?
Link: https://nocperu.com/es/component/content/article/8-noticias/1049-explicacion-que-es-el-peering-de-internet?Itemid=158
What are Bogon IPs?
General concepts:
Bogon IP addresses are those that are not valid on the public Internet and therefore cannot be used to route traffic through it. These IP addresses are reserved for private or internal use and are not assigned to devices on the public network.
There are several types of Bogon IP, but the most common ones are:
-
Private IP Addresses: These IP addresses are reserved for internal use on private networks, such as businesses or homes. Private IP addresses are used by devices on the local network to communicate with each other and are not accessible from the Internet. Some examples of private IP addresses are:
-
-
10.0.0.0 – 10.255.255.255
-
172.16.0.0 – 172.31.255.255
-
192.168.0.0 – 192.168.255.255
-
-
-
Unassigned or Retired IP Addresses: These IP addresses have not been assigned to any device or have been retired by IP address allocation registries. These addresses should not be used on any network and any traffic containing them should be blocked. Some examples of unassigned IP addresses include:
-
-
0.0.0.0 – 0.255.255.255
-
100.64.0.0 – 100.127.255.255
-
169.254.0.0 – 169.254.255.255
-
-
Security and Bogon IPs
Bogon IPs can be used by malicious attackers to try to hide their identity or to carry out attacks on an internal network. For example, an attacker might try to send malicious traffic from an unassigned IP address to evade intrusion detection systems.
To protect against potential threats, many organizations use IP Bogon filters to block traffic coming from these invalid addresses and to prevent external attacks on their network. It is also important to ensure that devices on the internal network use private IP addresses and not public IP addresses that could interfere with traffic on the Internet.
List of Bogon IPs
- 0.0.0.0/8 reserved for self-identification [RFC1122] , section 3.2.1.3
- 10.0.0.0/8 (10.xxx) reserved for Private-Use Networks [RFC1918]
- 100.64.0.0/10 reserved for Shared Address Space [RFC6598]
- 127.0.0.0/8 reserved for Loopback [RFC1122], section 3.2.1.3
- 169.254.0.0/16 reserved for Link Local [RFC3927]
- 172.16.0.0/12 (172.16.xx – 172.31.xx) reserved for Private-Use Networks [RFC1918]
- 192.0.2.0/24 reserved for TEST-NET-1 [RFC5737].
- 192.88.99.0/24 reserved for 6to4 Relay Anycast [RFC3068]
- 192.88.99.2/32 reserved for 6a44 Relay Anycast [RFC6751
- 192.168.0.0/16 (192.168.xx) reserved for Private-Use Networks [RFC1918]
- 192.0.0.0/24 reserved for IANA IPv4 Special Purpose Address Registry [RFC5736]
- 198.18.0.0/15 reserved for Network Interconnect Device Benchmark Testing [RFC2544]
- 198.51.100.0/24 reserved for TEST-NET-2 [RFC5737]
- 203.0.113.0/24 reserved for TEST-NET-3 [RFC5737]
- Multicast (formerly “Class D”) [RFC5771]
- Unicast-Prefix-Based IPv4 Multicast Addresses [RFC6034]
- Administratively Scoped IP Multicast [RFC2365]
- Reserved for future use (formerly “Class E”) [RFC1112]
- 255.255.255.255 is reserved for “limited broadcast” destination addresses [RFC919] and [RFC922]
In summary
In short, Bogon IPs are IP addresses that are not valid on the public Internet and are either reserved for internal use or unassigned. It is important to be aware of these addresses and take steps to protect yourself against potential threats.
To request security services: Send Whatsapp: https://nocperu.com/whatsappseguridad
Improve performance and scalability while reducing Bogon-related costs and resource consumption
Bogon filtering should only be undertaken if the impacts are well understood. These are not simple filters and can have adverse effects if applied incorrectly. In particular, see RFC6598 regarding 100.64.0.0/10. It is important that you understand your network and that any planned filters are rigorously tested before adoption. These filters may be more applicable to some devices, such as equipment acting as border routers, than to other devices.
Bogon tracking through routing registries is made possible by donations from several such registries. All of these objects track traditional IPv4 bogons, not the newer, more dynamic IPv4 and IPv6 fullbogons. To track fullbogons, you will need to use one of the other available data sources. You can find bogon objects in the following registries:
RADB
The good folks at Merit have donated a maintenance object within RADb for the cause. MAINT-BOGON-FILTERS contains three sets of filters:
-
fltr-sin asignar: Unassigned IPv4 prefixes (by IANA).
-
fltr-marciano: Reserved and special-use IPv4 prefixes.
-
fltr-bogones: The combination of fltr-unallocated + fltr-martian.
Details about RADb and objects can be found via WHOIS, for example:
whois -h whois.radb.net <nombre del conjunto de filtros>Let's talk more about the Bogons.
Introduction:
In the ever-evolving Internet landscape, a peculiar term called “Bogons” pops up from time to time. While it may seem whimsical or obscure, bogons have significant implications for high-level stakeholders and IT professionals. In this blog post, we’ll delve into the world of bogons, exploring three compelling reasons why high-level stakeholders should be motivated to take action, followed by three reasons why IT security and operations should care about bogons.
Part 1: What are Bogons?
Bogons are like people who show up with fake reservations at your favorite restaurant; they'll take up your reserved table while you keep pestering them. In the world of computers and networks, these 'bogons' are like mysterious guests who shouldn't be there but somehow slip away, bringing with them tangible business risks.
'Bogons' are IP addresses or network blocks that shouldn't exist on the Internet. They're either reserved for private use and aren't assigned to anyone, or they're reclaimed and put on hold by the Regional Internet Registry (RIR). Most bogons look and function like regular IP addresses, so your network devices won't necessarily take any action by default when they detect bogon-related traffic. But since using bogons on the public Internet already violates accepted best practices, it's highly likely that anyone using them has malicious intentions in mind.
Just as you wouldn't want unsavory or fake guests in a restaurant to cause chaos, networks don't want bogons to cause any trouble. They can cause a variety of problems, such as unauthorized access attempts, network congestion, or data leaks. It's as if these rude guests are trying to disrupt the evening on purpose.
Secure networks use filtering systems to identify and block bogons, just as you would have a reservation reference at the entrance of a restaurant to prevent unauthorized guests from entering. The filtering system checks incoming and outgoing network traffic, ensuring that only valid IP addresses can pass through. In this way, the network remains orderly, secure, and runs efficiently.
By filtering out buffoons, networks can focus on legitimate traffic and avoid wasting resources on those mysterious, unnecessary addresses. It's like having a well-managed reservation system that only accepts genuine customers, making your restaurant experience safer and more efficient.
In short, bogons are like unwanted guests in a restaurant that shouldn't be there. They are IP addresses that don't belong to or are assigned to anyone on the Internet. Filtering bogons from network traffic is crucial to maintaining security, efficiency, and proper operation, just as keeping unauthorized guests out of a restaurant ensures a smooth dining experience.
Part 2: Reasons for key stakeholders to act
Reputation and brand protection:
High-level stakeholders know the importance of maintaining a strong reputation and brand image. Accepting or transmitting bogon-related network traffic shows a general disregard for Internet best practices and lax enforcement of security standards. In particular, network service providers must take all necessary measures to prevent bogons from entering or leaving their networks, including those of their customers. Bogons are often used for DDoS (distributed denial of service) and data breach attacks, so even if bogons don’t directly affect you, they may travel through your network to affect others. By running a clean network and implementing appropriate filtering mechanisms (bogon and otherwise), organizations can safeguard the integrity of their brand and maintain the trust of their customers and partners.
Ensure regulatory compliance:
Compliance with privacy and data protection regulations is critical to business operations in today’s digital age. Ignoring compliance errors can expose organizations to compliance violations and compromises, which can result in legal repercussions and financial penalties. Taking a proactive approach to identifying and filtering compliance errors demonstrates a commitment to maintaining a secure and compliant infrastructure, which can help high-level stakeholders avoid legal issues and ensure a strong governance framework.
Operational risk mitigation:
Bogons can introduce operational risks by consuming network resources, leading to unnecessary costs, performance degradation, or service interruptions. These unapproved addresses can saturate network traffic and divert valuable resources, impacting the overall efficiency of IT operations. By addressing the issues, senior stakeholders can minimize risks, optimize network performance, and ensure uninterrupted functions, improving productivity and customer satisfaction.
Part 3: Why IT Security and Operations Should Be “Proactive”
Improving network security:
Bogons are often associated with malicious activity, so it is a priority for cybersecurity teams to identify and mitigate them. Attackers can leverage unassigned or invalid addresses within bogon prefixes to launch attacks, infiltrate networks, or disguise their malicious activities.
Implementing effective bogon filtering mechanisms strengthens network security by:
- preventing unauthorized access attempts
- reducing the attack surface
- Improve threat detection capabilities.
How to avoid false positives and misconfigurations:
Bogons can contribute to false positives and misconfigurations in security systems and network devices. Without proper filtering, security solutions can mistakenly flag bogon addresses as potential threats, triggering unnecessary alerts and burdening security teams. Additionally, misconfigured systems or devices can inadvertently allow bogon traffic, undermining the effectiveness of security measures. By actively addressing bogons, IT professionals can:
-
Minimize false positives
-
streamline incident response efforts
-
Optimize security operations.
How to ensure efficient resource allocation:
Bogons consume valuable network resources, including bandwidth, processing power, and storage. This inefficient allocation of resources can impact overall system performance, resulting in degraded user experience and reduced operational efficiency. By implementing robust bogon filtering mechanisms, IT operations teams can:
-
Reclaim these resources, optimize network utilization, and ensure efficient allocation for critical business functions.
-
Improve performance, scalability and profitability
Conclusion
Despite their whimsical name, bogons pose tangible risks and challenges for organizations across all industries. By understanding the motivations of high-level stakeholders and recognizing concerns about IT security and operations, organizations can take proactive steps to address the issues. Implementing effective filtering mechanisms, investing in network security measures, and optimizing resource allocation will enhance an organization’s cybersecurity posture and improve reputation, regulatory compliance, and operational efficiency. Embracing the battle against bogons is essential to navigating the ever-changing cybersecurity landscape and safeguarding digital infrastructure in today’s interconnected world.
Recomendations
Don't panic. However, bogon filtering is not trivial and requires careful planning and execution to ensure minimal disruption to services, networks, and infrastructure. The complexity of bogon filtering is compounded by the fact that specific bogon filtering lists can change on a daily basis. One day, an IP is a bogon; the next week, it may be a valid IP address. However, with some examples of significantly related web server traffic volumes, the challenges are worth the reward. SOCPERU provides free access and reliable, constantly updated tools to help organizations filter bogon IPs. These tools integrate seamlessly into your web servers, firewalls, routers, and monitoring systems. Bogons are likely to pose a potential risk or direct threat to your organization.
What you need to know beforehand
By filtering Bogon IPs using our free Bogon referral community service, you will significantly reduce the risk of DDoS attacks and malicious traffic, ensuring a more robust and reliable network.
Network awareness: Before you perform bogon filtering, thoroughly understand its implications. It is essential that you understand your network and the effects of bogon filtering.
List dynamics: Bogon lists, especially the full bogon list, change frequently. Make sure your filters are updated regularly to avoid inadvertently blocking legitimate traffic.
Peering Configuration: Ensure that you are able to perform multi-hop peering with a private ASN. Misconfigured peering sessions, particularly those that route bogon packets to us, will be dropped to maintain our quality of service.
Ability: Be prepared to accommodate up to 100 prefixes for traditional bogons and up to 250,000 prefixes for full bogons.
Updates and maintenance: Aggressive input and output filtering requires constant maintenance. We offer multiple formats and methods for receiving updates, ensuring you have the most recent data at hand.
Data sources: Our data is based on relevant RFCs, the IANA IPv4 allocation list (IPv4 summary page) and RIR data.
You will find the settings to use below. Don't forget that your password will be updated.
Information and settings: Enviar Whatsapp https://ixp.org.pe/whatsapeame
MIKROTIK Version 7 Initial Script
-
38.0.0.0/28 REPLACED BY ITS IPV4 BLOCK
-
38.38.38.1 REPLACES WITH YOUR FIRST IP IN IPV4
-
2803:ffff::/43 REPLACE IPV6 PREFIX WITH YOUR IPV6 BLOCK
-
tcp-md5-key=abcdefg12345678 REPLACE KEY WITH THE ONE THAT WILL BE GIVEN
-
.as=66666 REPLACE ASN WITH THE ONE THAT WILL BE GIVEN
-
remote.address=179.69.69.169/32 REPLACE IPv6 WITH THE ONE THAT WILL BE GIVEN
-
remote.address=2803:8888:abcd::1234/128 REPLACE IPv6 WITH THE ONE THAT WILL BE GIVEN
PART 01:
/routing bgp template
add address-families=ip as=64120 cisco-vpls-nlri-len-fmt=auto-bits disabled=\
no name="NOCPERU-IPV4" routing-table=main
add address-families=ipv6 as=6414 cisco-vpls-nlri-len-fmt=auto-bits disabled=\
no name="NOCPERU-IPV6" routing-table=main
/routing bgp connection
add address-families=ip as=64999 cisco-vpls-nlri-len-fmt=auto-bits connect=\
yes disabled=no hold-time=30s input.filter=BGP-NOCPERU-IN listen=yes \
local.address=38.38.38.1 .role=ebgp tcp-md5-key=abcdefg12345678 multihop=yes name=\
"NOCPERU.COM - IPV4 SISTEMA SEGURIDAD" output.filter-chain=\
BGP-NOCPERU-OUT .network=bgp-networks remote.address=179.69.69.169/32 \
.as=64120 .port=179 router-id=38.38.38.1 routing-table=main templates=\
"NOCPERU-IPV4"
add address-families=ipv6 as=6414 cisco-vpls-nlri-len-fmt=auto-bits connect=\
yes disabled=no hold-time=30s input.filter=BGP-NOCPERU-IN listen=yes \
local.role=ebgp tcp-md5-key=abcdefg12345678 multihop=yes name="NOCPERU.COM - IPV6 SISTEMA SEGURIDAD" \
output.filter-chain=BGP-NOCPERU-OUT .network=bgp-networks .redistribute=\
connected,static,rip,ospf,bgp,vpn,dhcp remote.address=\
2803:8888:abcd::1234/128 .port=179 router-id=38.38.38.1 routing-table=\
main templates="NOCPERU-IPV6"
/routing filter rule
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 64496:0) { set blackhole yes; accept; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 65332:888) { set blackhole yes; accept; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 64496:0) { reject; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 65332:888) { reject; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 6414:0) { set blackhole yes; accept; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 64120:0) { set blackhole yes; accept; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 65332:888) { set blackhole yes; accept; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 6414:0) { reject; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 64120:0) { reject; }"
add chain=BGP-NOCPERU-IN disabled=no rule=\
"if (bgp-communities includes 65332:888) { reject; }"
add chain=BGP-NOCPERU-OUT disabled=no rule="reject;"
add chain=BOGON-SERVER-IN disabled=no rule=\
"if (bgp-communities includes 65332:888) { set blackhole yes; accept; }"
add chain=BOGON-SERVER-IN disabled=no \
rule="reject;"
add chain=BOGON-SERVER-IN disabled=no rule=\
"if (bgp-communities includes 65332:888) { }"
add chain=BOGON-SERVER-OUT disabled=no rule=\
"reject;"
PART 2:
-
dst-address=164.9.9.9.1 REPLACE IPv4 WITH THE ONE THAT WILL BE GIVEN
-
src-address=179.60.7.7.1 REPLACE IPv4 WITH THE ONE THAT WILL BE GIVEN
-
dst-address=2604:aaaa::1 REPLACE IPv6 WITH THE ONE THAT WILL BE GIVEN
-
src-address=2803:ffff::1 REPLACE IPv6 WITH THE ONE THAT WILL BE GIVEN
/ip traffic-flow
set enabled=yes
/ip traffic-flow target
add dst-address=164.9.9.9.1 port=8888 src-address=179.60.7.7.1
add dst-address=2604:aaaa::1 port=8891 src-address=2803:ffff::1
/system clock
set time-zone-name=America/Lima
/system ntp client
set enabled=yes
/system ntp client servers
add address=200.186.125.195
add address=64.90.182.55
/ipv6 firewall filter
add action=accept chain=input comment="Allow limited ICMP - PING" limit=\
50/5s,5:packet protocol=icmpv6
add action=accept chain=input comment="limited ICMP input PING" limit=\
100,5:packet protocol=icmpv6
add action=drop chain=input comment="BLOCK PING FROM WAN" protocol=icmpv6
/ip firewall filter
add action=accept chain=input comment="Allow limited ICMP - PING" limit=50/5s,5:packet protocol=icmp
add action=accept chain=forward comment="limited ICMP input PING" limit=100,5:packet protocol=icmp
add action=drop chain=input comment="BLOCK PING FROM WAN" limit=100,5:packet protocol=icmp
VERSION 6:
/system clock
set time-zone-name=America/Lima
/system ntp client
set enabled=yes primary-ntp=200.186.125.195 secondary-ntp=64.90.182.55
IP to ASN Mapping Service
Automate and streamline WHOIS lookups to save time and improve security.
IP to ASN mapping is not a GeoIP service!
The country code, registry and assignment date are based on data obtained directly from regional registries including: ARIN, RIPE, AFRINIC, APNIC and LACNIC. The information returned for these categories will be as accurate as the information present in the RIR databases.
IMPORTANT NOTE: Country codes are likely to vary significantly from actual IP locations, and we strongly recommend that the IP to ASN mapping tool not be used as an IP geolocation (GeoIP) service.
The exact links for each of the data sets are as follows:
ftp.arin.net/pub/stats/arin/delegated-arin-extended-latest
ftp.ripe.net/ripe/stats/ripencc-delegado-más-reciente
ftp.afrinic.net/pub/stats/afrinic/delegated-afrinic-latest
ftp.apnic.net/pub/stats/apnic/delegated-apnic-latest
ftp.lacnic.net/pub/stats/lacnic/delegated-lacnic-latest
ASN descriptions are based on data obtained from cidr-report.
Looking for an IP geolocation service?
If you are looking for an IP geolocation service, please check out one of the following (note: links do not constitute a recommendation):
-
MaxMind
-
IP2Location
-
Neustar
-
ipinfo.io
-
ipdata.io
-
ipgeolocation.io
-
ipregistry
-
Big Data Cloud
-
ipwhois.io